January Consumer Cyber Safety Pulse Report – From Norton Labs
What you need to know about COVID-19, dating, and Squid Game scams (and why they won’t go away). Plus, online tracking, Tax Day scams and the year’s greatest hacks
You might expect a new year to ring out the old and ring in the new, but that is not the case when it comes to your Cyber Safety in 2022. Old threats to your online privacy and security are likely to overstay their welcome, and new threats are always on deck.
We crunched the numbers for our quarterly Consumer Cyber Safety Pulse Report, and we’re looking back at cyber threats from the final three months of the year, plus we’ve captured a full overview of 2021.
In this Pulse Report, the Norton Labs team rounds up noteworthy phishing finds, uncovers online tracking, reports on threats of tax fraud, and digs into 2021 top exploits and breaches.
Cyber Safety threats by the numbers
NortonLifeLock technology has blocked almost 10 million threats on an average day in 2021. Here’s a closer look at the numbers from October through December and for all of 2021.
.jpg15a3.webp)
_2.jpg27a5.webp)
_1.jpg2ae0.webp)
Spotlight #1 – Recent Phishing and Scam Samples
Phishing emails and scams top the list of threats. Each quarter we like to highlight some of the more interesting or unique pages that we have recently found. Three themes this past quarter were COVID-19, cupid, and culture.
- COVID-19 scams. Goal: Steal your personal information and money.
- Dating website scams. Goal: There is no love to be found here. These scammers only want your personal information.
- Pop-culture scams. Goal: Swipe your sensitive information and cash for trendy but fake items. Free Squid Game apparel, anyone?
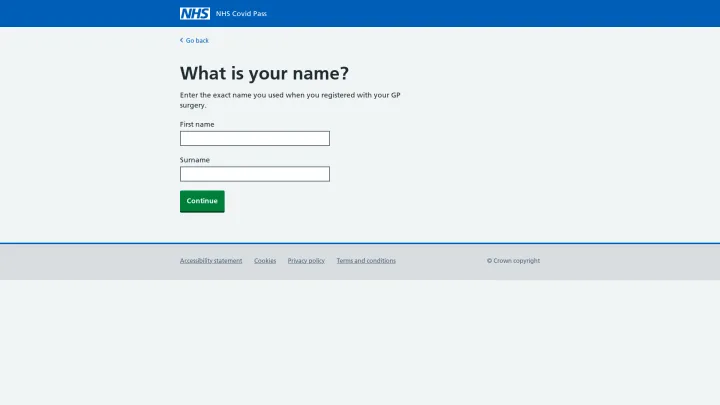
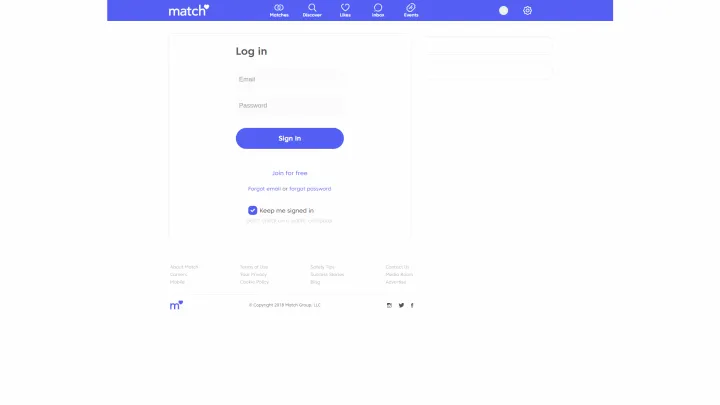
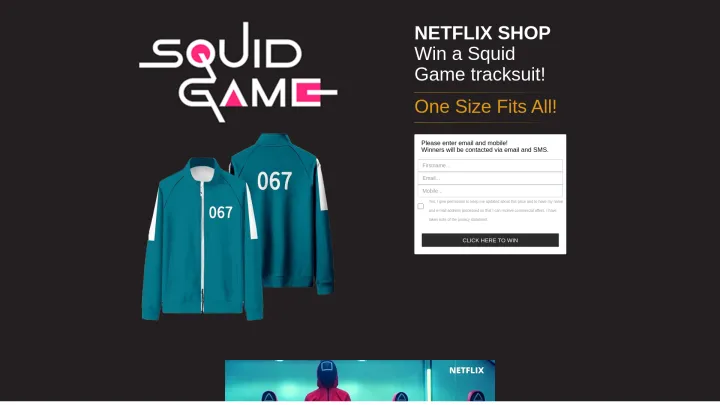
Spotlight #2 – Online Tracking
It’s common knowledge that web trackers know an astonishing amount of information about you. Our new research discovered that sometimes they know as much as twice what was previously found. And even if you delete your browser's data history, they can reconstruct your “data identity” within hours.
Background:
Web tracking keeps tabs of what you do online. It plays a role in the web advertising industry and is the target of legislative efforts to rein it in.
Can trackers really track every movement of web users? Pretty much.
How it works:
We looked at how web trackers are following users around the internet. We found previous studies may underestimate the knowledge that trackers have and how quickly they collect this information.
Surprises we found:
- Top Trackers: Our study reveals that top trackers can see 73% of an average user’s browsing history despite appearing on a smaller number of unique domains.
- The power of sharing: We also estimate how much additional knowledge organizations can gain if they cooperate. Two organizations would see a 5% bump if they shared data; more than two organizations cooperating could push that number up to 50%.
- Getting to know you — quickly: Consumers encounter, on average, 177 tracking organizations in one week, they will encounter half of those trackers in the first two hours of browsing. In other words, if the user were to start over with a fresh browser, it would only take two hours on average to re-encounter 50% of all trackers.
Advice for consumers:
Web trackers have a vested interest in knowing as much about you as is technologically possible. It doesn’t have to be that way. You can take steps to protect your web activities from snoops. For instance, a VPN and private browsing can help. NortonLifeLock also developed Norton AntiTrack to help. https://us.norton.com/norton-antitrack
Learn more:
Read the full report “When Sally Met Trackers” or check out the blog posts:
- https://www.nortonlifelock.com/blogs/norton-labs/online-trackers
- https://www.nortonlifelock.com/blogs/norton-labs/norton-antitrack
Spotlight #3 – Tax Scams and Identity
Tax season is upon us in the U.S., and fraudsters are ready to pounce. Get ready for fake IRS calls and tax-related identity theft.
Background:
Tax time can make you feel uniquely vulnerable. You might be overwhelmed by the thought of owing or receiving money. You might fear the power of the IRS or feel anxious about providing more details to the government than you would in other situations. This is a potentially dangerous combination, and we’re seeing an uptick in scams designed to prey on those emotions.
How it works:
A scammer will create a false sense of urgency by sending you a carefully crafted phishing email or text message, informing you of a limited time to claim child tax credits, for example. The email will then direct you to a fake IRS phishing page where it will ask you to log in using your username and password or collect your Social Security number, date of birth, as well as other types of private information.
Normally, you’re probably conditioned to keep most of this information private. But when the “government” asks? It’s one of those times when you might be willing, and even expect, to provide sensitive personal information.
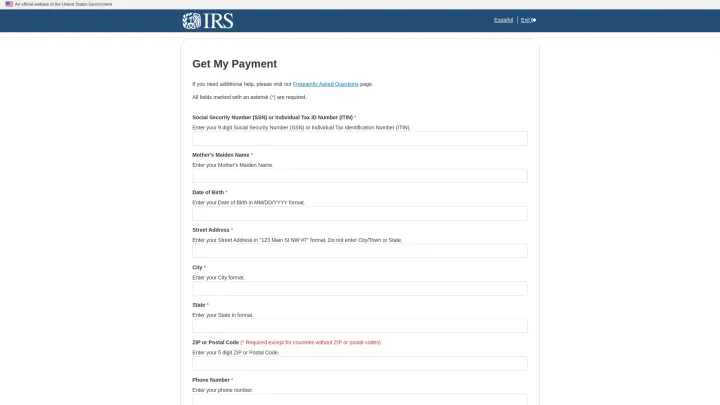
What might happen next? Scammers can use this information to access your financial information and commit fraud in your name.
What we have seen so far:
The chart below shows the number of unique malicious URLs that we detected spoofing IRS web pages. You can see a few sustained spikes starting in June 2021 and another in December 2021.

They capture moments when attackers spotted an opportunity.
- The first sustained spike in June coincides with the introduction of the child tax credit (the first payment went out on July 15, 2021).
- The second spike at the end of 2021 appears to be a similar effort to take advantage of the fact that the program was ending.
Both events were in the news and primed people to provide personal information on themselves and their dependents. Scammers capitalize on news stories to adapt their lures to trick their victims.
What are the threats:
Another threat to your taxes is tax-related identity theft. That’s when someone else files a tax return in your name to collect your refund before you do. When you go to file, IRS records show that you have already done so — and the headache begins.
This can happen if your personal information is stolen in a phishing attack like in the above Figure. It can also happen if enough of your data is exposed through other sources, like data breaches or because of a malware infection on your device.
Tip:
One way to prevent this type of fraudulent filing is to sign up early for an Identity Protection PIN. An IP PIN is a form of multifactor authentication that the IRS offers to all taxpayers. Once you sign up, your IP PIN is required when you file your taxes and acts as a secret key that only the filer and the IRS should know. You can learn more from our blog post on the topic or from the IRS webpage.
The IRS is adding an extra security layer to obtain a pin or view your data, but that will not go into effect until summer of 2022 and may not even cover filing your taxes since many people file without ever obtaining a PIN.
Bottom line:
This tax season, be on the lookout for scammers — because the scammers are on the lookout for you.
Advice for consumers:
- Your identity matters. It’s a good idea to be careful when giving out your personal information and be aware that your data may already be out there due to past breaches.
- The IRS does not use email, text messages, or social media to communicate with taxpayers about tax matters. If you receive an unsolicited email from the IRS asking you to confirm your personal information, then it's highly likely to be a phishing fraud. Delete it at once and report it.
- Get your unique IP PIN to prevent others from filing on your behalf (and keep it safe and secure).
Learn more: Check out the blog
- https://us.norton.com/internetsecurity-id-theft-what-is-an-ip-pin.html
- https://www.nortonlifelock.com/blogs/security-response/tax-refund-scams
Spotlight #4 – A big year for exploits and breaches
You might like to breathe a sigh of relief that the hacks and breaches of 2021 are behind us. But not so fast. You might feel the effects of some of these cybercrimes for years. Presenting the highlights (and low lights) of the year:
Background:
First, consider the breadth of the most notable data breaches of 2021. They included the trading platform Robinhood, the streaming platform for gamers Twitch, and the adult site Stripchat.
Next, consider the business-focused social media site LinkedIn, which was the target of an information scraping attack that — while not a breach — allowed attackers to gather a trove of information from the site.
If the breaches were notable, the hacks were extraordinary. Consider these three:
- A vulnerability in software maker Kaseya’s VSA software led to thousands of managed businesses infected with malware through the companies they pay to manage their networks and systems.
- A supplier of spyware sold to intelligence agencies and police, NSO Group, was the focus of a coordinated exposé in multiple news outlets.
- Not to be outdone, the ongoing saga of the Log4shell vulnerability has continued in the news cycle, creating concerns for consumers and businesses alike.
Breach roundup:
LinkedIn scrape: Though originally suspected to be an actual breach, an investigation in April 2021 revealed that LinkedIn’s website had been scraped, collecting public information of more than 700 million users. After failing to sell the data, it was dumped for all to see. [1]
Twitch incident: The well-known gamer streaming platform Twitch confirmed it was the target of a data breach in October 2021, of which more than 100GB was posted online. Included in the dumped data were earnings of one of the platform’s most popular streamers over the past two years. Most damaging to the company, however, was their acknowledgement that the breach also included the source code that drives their platform. [2]
Stripchat breach: In November of 2021 the adult webcam site Stripchat revealed that 200 million records were stolen by cybercriminals. The breach was particularly concerning as it contained not only personal identifiable information (PII) of customers and some of the models, but also more than 700,000 private messages that could eventually lead to blackmail. [3]
Robinhood incident: Also in November of 2021, online trading platform Robinhood disclosed a breach of about 300 of their customers. The breach was significant not in scale, but because it was the result of attackers using social engineering to convince an internal Robinhood support representative to disclose information that led to the compromise — all over a phone call. [4]
Hack roundup:
Kaseya vulnerability. In July 2021, nearly 2,000 companies whose networks and computers are maintained by managed services companies were infected with ransomware after a vulnerability was discovered in the Kaseya VSA software used by managed services companies. A well-known criminal gang known as REvil took credit for the attack and said the operation infected more than a million systems. [5]
Pegasus spyware. The Pegasus Project coordinated publications in July of 2021 through multiple news outlets, detailing alleged abuses of the Pegasus spyware program made by the Israeli firm NSO group. Since the disclosures, more articles detailing further abuses have been published leading to a lawsuit from Apple and the company being blacklisted by the U.S. Department of Commerce. [6]
Log4j. In November 2021, a critical bug was found in the Log4j software package used in Java — and potentially billions of devices worldwide. The ease with which the bug, nicknamed Log4shell, can be exploited — and the fact that it allows attackers to do nearly anything they want on affected systems — established the vulnerability as the most severe in a decade. [7]
Bottom line:
Though 2021 brought some significant data breaches and concerning hacks, the global cybersecurity community has once again coordinated to share information and develop systems to help businesses and consumers.
Learn more by checking out these links:
- [1] https://news.linkedin.com/2021/april/an-update-from-linkedin
- [2] https://blog.twitch.tv/en/2021/10/15/updates-on-the-twitch-security-incident/
- [3] https://stripchat.com/blog/temporary-server-breach-identified/
- [4] https://blog.robinhood.com/news/2021/11/8/data-security-incident
- [5] https://helpdesk.kaseya.com/hc/en-gb/articles/4403584098961-Incident-Overview-Technical-Details
- [6] https://forbiddenstories.org/case/the-pegasus-project/
- [7] https://www.nortonlifelock.com/blogs/norton-labs/what-log4j
Looking ahead
Norton Labs continues to track scams and threats targeting consumers. Find out more when we publish our next Consumer Cyber Safety Pulse Report in April.
Editorial note: Our articles provide educational information for you. NortonLifeLock offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about cyber safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses.
Copyright © 2022 NortonLifeLock Inc. All rights reserved. NortonLifeLock, the NortonLifeLock Logo, the Checkmark Logo, Norton, LifeLock, and the LockMan Logo are trademarks or registered trademarks of NortonLifeLock Inc. or its affiliates in the United States and other countries. Other names may be trademarks of their respective owners.






.jpg54e6.webp)
We encourage you to share your thoughts on your favorite social platform.